Security Policy Review Audit Work Program
A Sample for Assessing and Developing IT and Data Security Policies
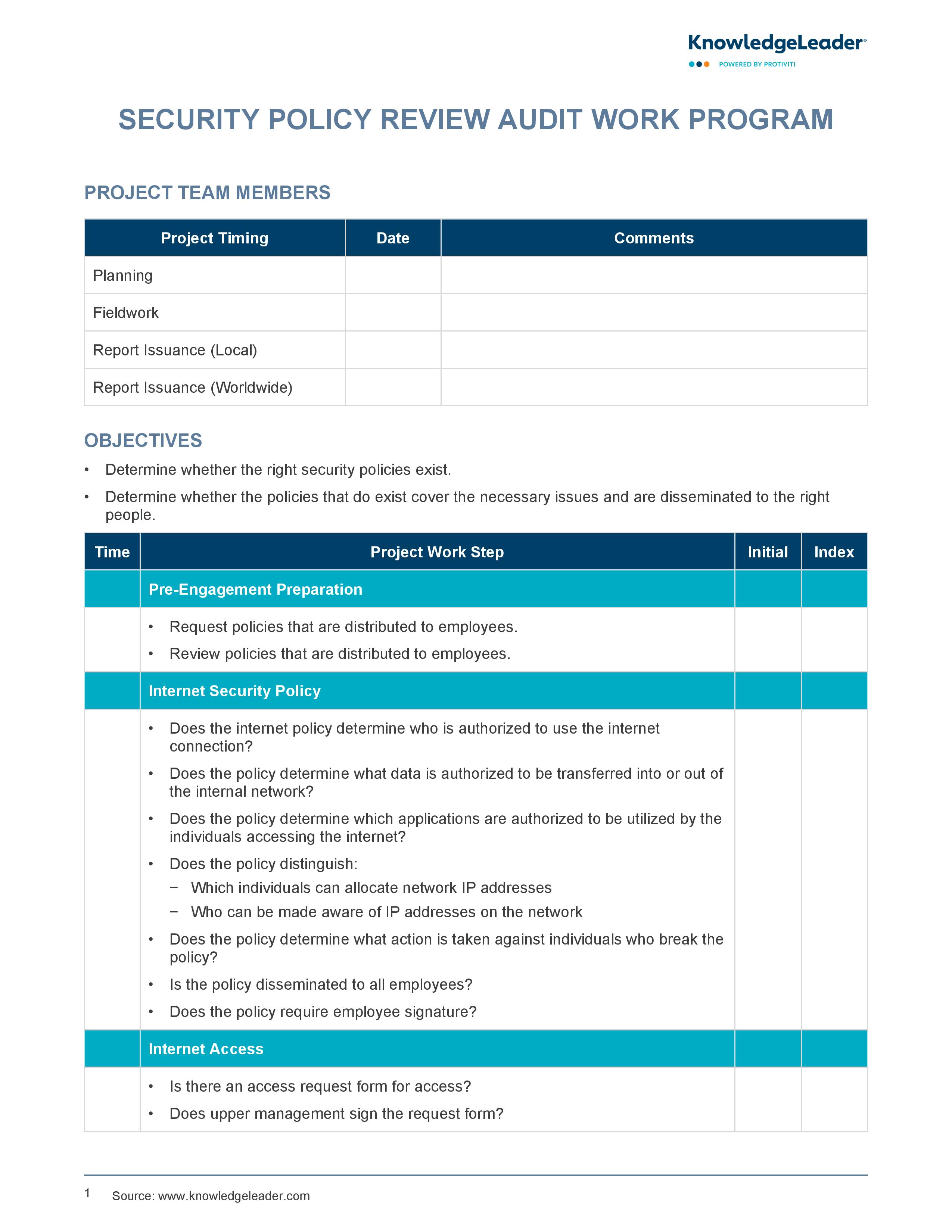
The purpose of this sample audit work program is to determine the adequacy and effectiveness of security policies that govern various aspects of an organization’s IT and data handling practices. It covers a wide range of policies, including internet usage, data confidentiality, email, voicemail, personnel computer controls and social engineering, among others. Each section of the document outlines specific objectives and steps to review the existing policies, such as checking if the policies are well-distributed among employees.
The document also provides a structured approach for the audit process by including pre-engagement preparations, fieldwork and report issuance phases. By using this work program, organizations can ensure that their security policies are not only comprehensive and up to date but also effectively communicated and enforced across the organization. This helps in safeguarding sensitive information and maintaining robust security standards to mitigate potential risks and vulnerabilities.
Sample questions include:
- Is there a data confidentiality policy?
- Does the policy include all data processing resources?
- Are the individuals responsible for ensuring that resources are secured named?
- Does the policy cover emergencies?