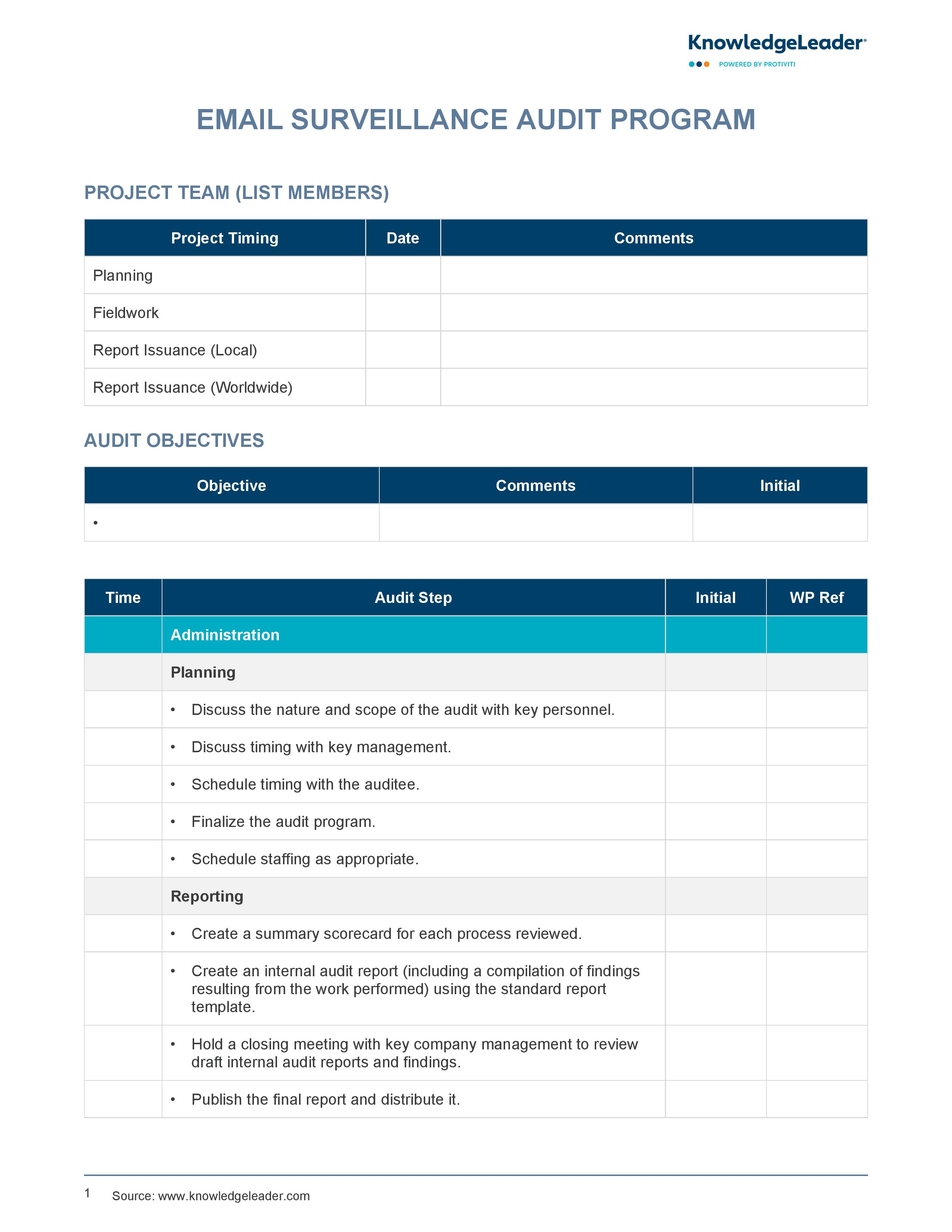
Email Surveillance Audit Program
Best Practices for Effective Email Surveillance Audits
Utilize our Email Surveillance Audit Program to enhance data privacy within your organization. This program outlines critical procedures for planning, fieldwork and reporting, ensuring a structured approach to the audit process. The program helps assess the adequacy of policies related to email surveillance, including data privacy, security and compliance with organizational standards. It emphasizes reviewing roles and responsibilities, ensuring proper access controls, and verifying training on data privacy and code of conduct. This document can be used to examine processes for collecting, storing, analyzing and transmitting sensitive email data while maintaining traceability and security.
The program highlights the importance of securing analyzed email data, managing storage media, and ensuring compliance with encryption and authentication standards. By following the outlined steps, you can identify gaps, recommend improvements, and ensure that email surveillance activities align with organizational objectives and regulatory requirements. This document is a valuable tool for ensuring robust email surveillance controls and fostering accountability across all levels of management and operations.